Capabilities
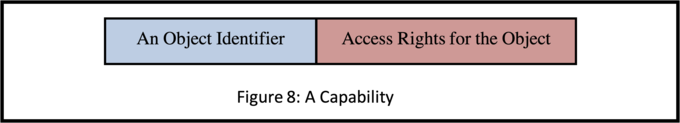
A capability (or reference) is a data structure which not only contains an object identifier that allows the object to be uniquely identified and located, but also a set of "access rights" [17] that specify the access rights for the object which can be invoked via the capability (see Figure 8).
In Monads and SPEEDOS there are 3 kinds of capabilities.
Capabilities within a program or file module are actually pointers to other internal structures of the same program or file module. The access rights associated with them can be read only, read write or execute. How these function in a Monads/SPEEDOS system are explained in section 7 of [18], which can be downloaded below.
A second level of capabilities, known as "module capabilities", allows a user whose process is active in one module to activate an entrypoint of a different module, and thus, for example, to activate the semantic routines of a file. The access rights in the capability consist primarily of bits in a bit list, where each bit, when set, indicates an entrypoint of the module that the caller can activate. If an access right bit is unset, the capability cannot be used to gain access to the module via that entrypoint. Module capabilities are used as operands to a kernel instruction for making inter-module calls (IMCs). Thus it is not only sufficient for a program to possess a capability for an object; it must have a capability with the access right set for the interface method which it wishes to call. There is also an "invalid bit" which means that the object cannot be accessed via this capability. A user can invalidate a capability, but cannot re-validate an invalid capability. Similarly the holder of a capability can reduce the access rights, but cannot reinstate it.
There are other rights in a capability, such as a right to copy or delete the capability.
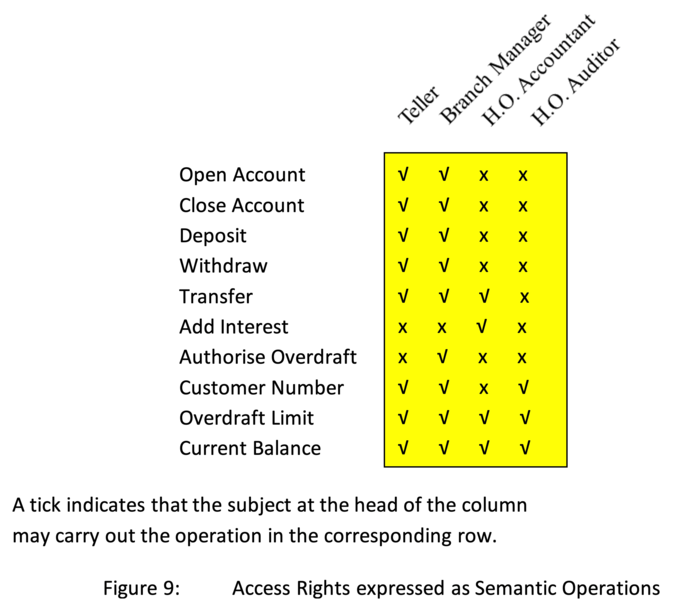
For example a capability for the bank account example in Figure 3 will potentially have access right bits corresponding to the semantic routines Open Account, Close Account, Deposit, Withdraw, etc. (see Figure 9).
Only those processes/threads which have a valid capability with the "add interest" right set will be able to call the routine that adds interest to the bank account instance. Thus it is possible to allow the teller's program to have a capability which has rights for example to open and close accounts and make deposits for customers, but not to add interest or to authorise an overdraft. These rights could for example be reserved for the programs in the accountant's department and/or for managers.
Finally SPEEDOS provides a number of kernel instructions, some of which can only be executed if the calling thread can present a valid kernel capability as an operand. Other kernel instructions, such as the inter-module call (IMC), are unprivileged and can be executed by any thread (but can of course fail in appropriate cases).
SPEEDOS also has other ways of protecting information (which can be used for example to revoke a capability), but these depend on other features of SPEEDOS which are not described here; these can be found in Making Computers Secure, volume 2, which can be downloaded below.